One of the main challenges faced by this advance is to develop systems so that people are able to prove their identity in the digital environment, in short, so that everyone can prove unequivocally that they are who they say they are in order to carry out these processes and cannot be done by someone else in your place. That is why, as a result of this challenge, concepts such as identification, authentication and authorization have emerged. Are you already familiar with them?
What is the difference between these concepts?
Identification is the ability to uniquely identify a user of a system or an application running on the system, while authentication is the ability to prove that a user or application is indeed who that person or application claims to be, and finally, authorization is the ability to specify access rights or privileges to resources and allow them, provided that identification has been ensured.
Currently to access an online service, you identify yourself through your name, email and/or username, you authenticate yourself through a security factor, for example password, as this is the most known and used security factor. But given the increase in cybercrime in recent years, and especially digital identity theft, authentication systems are becoming increasingly sophisticated, since the best known so far, are becoming obsolete because cybercriminals have found a way to bypass this security factor.
This type of new security factors are based on the behaviors or factors that make each human being unique. Behavioral security aims to capture, analyze, understand and respond to all kinds of digital representations of human behavior and interpret them using innovative technologies and machine learning algorithms.
Learning from human behavior could in many cases put an end to security breaches by identifying, eliminating and preventing anomalous or risky behavior, such as the identification and detection of false identities or credential theft, which can be used to access devices or services of different kinds and thus jeopardize the security of systems.
Ironchip and localization behavior.
The best way is to add innovative security layers that take into account the identity of the device from which the service is accessed, and that use secure communication channels and factors that are more difficult to spoof. This is why we at Ironchip are launching a unique technology to the market, Location-Based Security, our AI that uses the location generated from environmental waves as a safety factor.
In Ironchip we analyze the behavior of human beings in their daily relationship with these online services, to reach the conclusion that the locations from which we access each of the services in the day to day are intimately linked to our behavior and the service in question. We do not make a large money transaction from a bar, we try to do it from safe spaces such as our home, the office... We do not access protected services from our professional environment in the street, but we do it from the office...
Therefore, we researched and learned that mobility behavior makes each human being unique, the places we frequent in our day are a set of data that can identify us in a specific way just like our date of birth, name or ID card, thus becoming another factor of our identity.
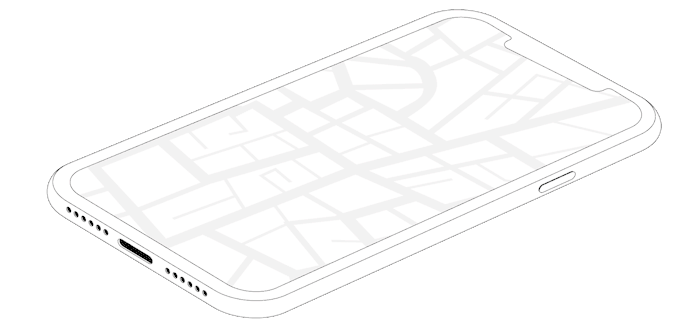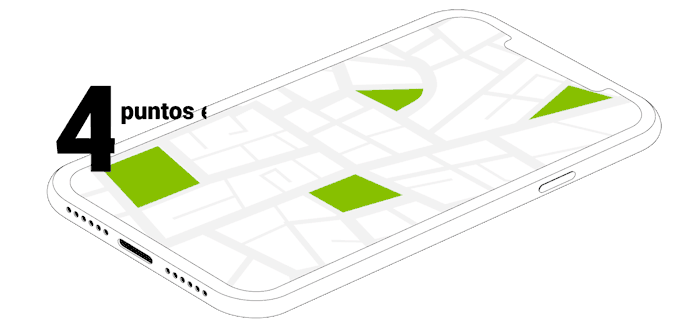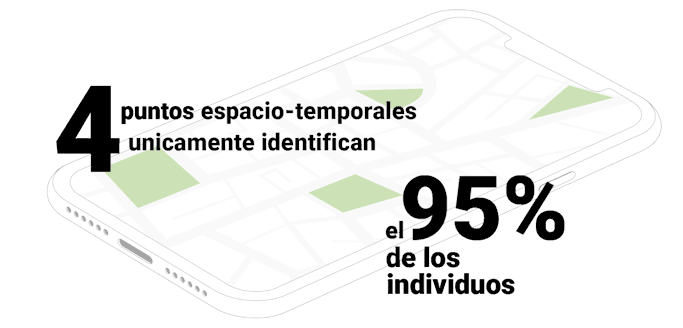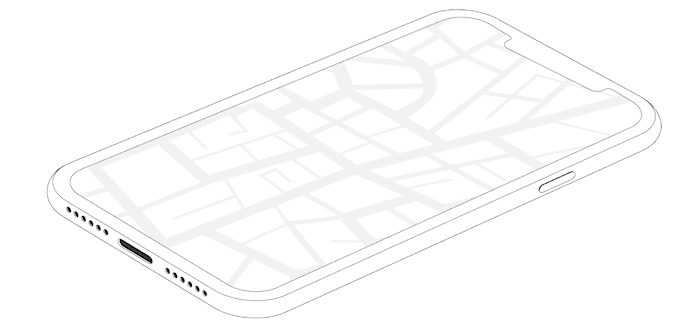
The study Unique in the Crowd: The privacy bounds of human mobility published on March 25, 2013 already spoke of the value of an individual's locations to be able to identify him unambiguously: "We studied for fifteen months the human mobility data of 1.5 million individuals and found that human mobility traces are highly unique. In fact, in a dataset where the location of an individual is specified every hour, and with a spatial resolution equal to that given by the carrier's antennas, four spatio-temporal points are sufficient to uniquely identify 95% of the individuals."
So why hasn't location been used to generate digital identity so far?
Localization as we know it to date (GPS and IP) presents several security and usability problems, which has meant that it has not been present in security systems up to now. The main problems can be summarized in the following points:
- Most geopositioning systems are based on coordinates, that is, using a GPS sensor the device obtains a latitude and longitude, which can be used to locate its position on a map. Although this is useful for most applications, it is not useful for cybersecurity, since any user with Google Maps can obtain coordinates and send a false location. Not only that, but there are hundreds of applications for mobile devices that allow sending false coordinates, so it is very easy for an attacker to impersonate, for example, the location of our house.
- Geolocation requires a GPS sensor, something that not all devices include, preventing its use in certain equipment, such as laptops or desktops.
- Location systems such as GPS and IP are provided from the user's device and this affects the privacy of the individual.
How does Ironchip solve these problems?
La Ironchip's location technology is highly resistant to location spoofing, it analyzes the waves detected by a device in a specific location, creating a digital identity to recognize trusted users based on their unique behavior patterns.
To achieve a truly secure location that is difficult to spoof, we have replaced the typical latitude and longitude with more advanced geolocation methods, based on Artificial Intelligence and Big Data processes. Instead of using the GPS sensor, we are able to verify whether or not a device is in a secure location by signals from the environment, i.e. we analyze Wifi signals, signals from mobile devices such as 2G, 3G and 4G, or even from IoT signals such as Sigfox or Lora.
This technology puts an end to the problems of the current location by managing to generate a secure location capable of being used as proof of digital identity capable of proving identity in the digital environment, in short, that everyone can prove unequivocally that they are who they say they are by the relationship of the behavior of their locations.
By substituting coordinates for the set of analyzed signals, we prevent any remote attacker from spoofing our location. To do so, the attacker would have to be physically at the secure location, which makes the attack extremely difficult, and makes automated attacks impossible.
In addition, our technology is the first fully anonymous location alternative, since we do not know the coordinates of the location, only the waves, it is not possible to place this location on a map. Location data can easily become very sensitive, that is why Ironchip follows privacy by design in the development of our solution and we do not capture, store or associate any additional information with location data.
With Ironchip you will be able to protect your company and its employees in an easy, comfortable and secure way with our solutions, among which you can find:
- Secure third-party connectivity, control with Ironchip the access of suppliers to the company's most sensitive systems. The incorporation of third parties in the maintenance of systems, machinery and even in the production process is necessary, but this increases vulnerability and turns each access into a possible entry vector to compromise a company.
- Bank fraud detection system, Banks are alerted by Ironchip fraud detection systems about suspicious transactions made from the user's anomalous locations. It is possible to analyze the device, identity and location and prevent fraud in real time.
- Secure remote connections, guarantee with Ironchip the security of remote access to your services and corporate network. Integrate our MFA in any service in an agile and comfortable way and protect any remote access solution, both RDP and VPN, only allowing access from assigned locations to prevent unauthorized access.
- Get easy and secure user authentication, provide your employees with the easiest authentication system to use. Discover a solution 100% adaptable to your needs: integration into any service in an agile and comfortable way for high security requirements, verifying identity with three factors in a single interaction or even frictionless.
Protect yourself with Ironchip
To learn more, please fill out the form and we will contact you shortly.
Tags:
Ironchip solutionsAugust 12, 2022
