What about you? Which is your security level?
Digitization and the development of the internet means that each time our processes are carried out digitally and we access the vast majority of our services through the network on a daily basis: bank transactions, administrative requests, work processes, access to an online service... This is undoubtedly a great advance, but it also poses significant challenges in the security of our digital identity and the privacy of our personal data on the network.
One of the main challenges that this advance faces is to develop systems so that people can prove their identity in the digital sphere. In short, that everyone can unequivocally prove that they are who they say they are, in order to carry out these processes and they cannot be done by someone else in your place. This is the reason why concepts such as identification, authentication and authorization have emerged. Are you already familiar with them?
Which is the difference between these concepts?
La identificación es la capacidad de identificar de forma exclusiva a un usuario de un sistema o una aplicación que se está ejecutando en el sistema, mientras que la autenticación se trata de la capacidad de demostrar que un usuario o una aplicación es realmente quién dicha persona o aplicación asegura ser, para que por último, la autorización sea capaz de especificar los derechos o privilegios de acceso a los recursos y permitir estos, siempre que se haya garantizado la identificación.
Identification is the ability to uniquely identify a user of a system or an application running on the system, while authentication is the ability to prove that a user or application really is who that person or application says. Finally, the authorization specifies the privilegies of access to resources and allows them, provided that identification has been guaranteed.
Authentication, one of the biggest challenges
Currently, is you want to access an online service, you identify yourself with your name, email and/or username, you authenticate through a security factor, for example a password (this is the most well-known and used security factor). But given the increase in cybercrime in recent years, and especially digital identity theft, authentication systems are becoming increasingly sophisticated, since the best known systems are becoming obsolete due to the fact that cybercriminals have found a way to bypass this security factor.
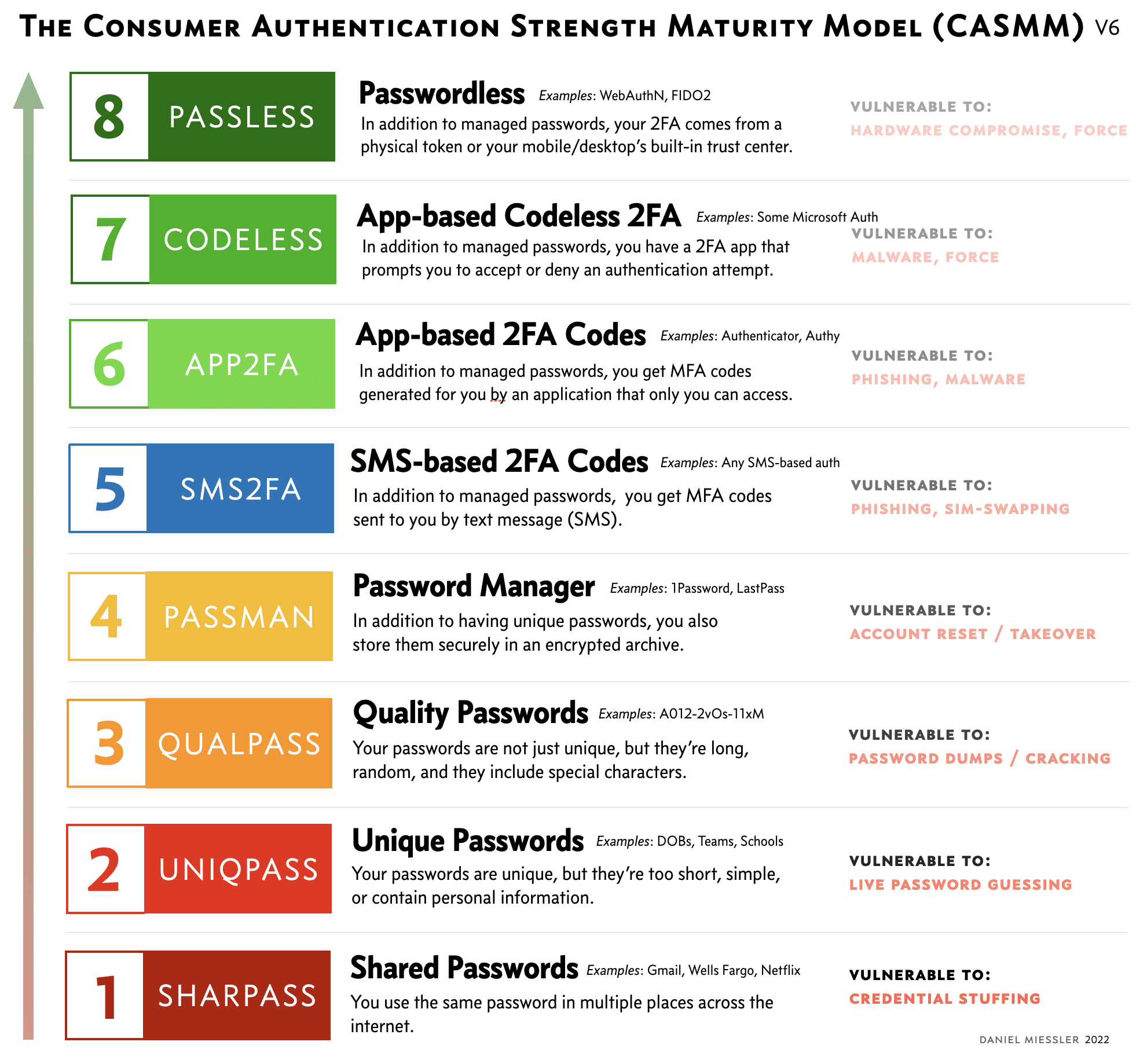
Are you protected? Which security level provides your authentication method?
CASMM, The consumer Authentication Strength Maturity Model is a visual reference designed to help security-conscious individuals protect themselves.
The majority of users live in levels 1, 2 and 3, which makes them vulnerable to the vast majority of cyber attacks. Level 4 enrolls all of your primary accounts in a password manager, which means using the password manager to create new, strong passwords and then changing them for those services. That, as we can see on the scale, although it is a good practice, it does not avoid the vulnerabilities posed by the use of passwords in an organization.
The next big jump is moving to level 5 or higher, which is the transition from password-only to multi-factor authentication (MFA). That transition is the most important. Once at level 5, the goal should be to get out of level 5, 6, 7, or 8. This is why level 5 (text/SMS based MFA) is by far the weakest form of MFA in the model.
That's why security and enhancement is at levels 7 and 8. At that stage, there are no MFA codes to steal. At these two levels, MFA authentication takes place transparently in the background, in a cryptographically secure way that never involves the user. And since the user never sees a code, that code cannot be stolen.
And here is where the importance of using Multiple Factor Authentication (MFA) is born. According to the official Google blog, the MFA has shown that the accounts compromised in cyber attacks were reduced by 50% after the application of this simple measure, which almost completely mitigates direct attacks on business email accounts.
Not all MFAs are the same, and the differences matter a lot
Currently, passless methods begin to exist, without passwords. These types of new safety factors are committed to being based on the behaviors or factors that make each human being unique. Learning from human behavior could in many cases put an end to security breaches, since it allows identifying, eliminating and avoiding anomalous or risky behavior, such as the identification and detection of false identities or theft of credentials, which can be used to access to devices or services of different kinds and thus put the security of the systems at risk.
The behavior of a human being is something inherent to him, like his ID or his appearance, from here identity factors such as the fingerprint or the face ID are born. What happens with these factors is that they are static factors, a static factor refers to any credentials that don't change or rarely change, like passwords, IP addresses, email address... facial features and fingerprints pose a problem similar to that of passwords... since changing the face or fingerprint is not something common or accessible. The big problem with using static authentication factors is that they have a high potential for being stolen.
How does Ironchip use user behaviour as a safety factor?
Having the behavior and the user as the epicenter of the company's security to facilitate the insertion of this type of cybersecure methods is not only the best that Ironchip can offer you. At Ironchip we analyze the behavior of human beings in their daily relationship with these online services, until we reach the conclusion that the locations from which we access each of the services on a day-to-day basis are closely linked to our behavior and to the service. We do not make a large money transaction from a bar, we try to do it from safe spaces such as our home, the office... We do not access protected services of our professional environment on the street, but we do it from the office...
Ironchip´s location technology is highly resistant to location spoofing, analyzing the waves a device detects in a particular location, creating a digital identity to recognize trusted users based on their unique behavioral patterns.
Why should you choose Ironchip MFA over other authentication systems?
With Ironchip you can protect your company and its employees in an easy, comfortable and safe way with our smart location. Our security software detects unauthorized access by transparently learning the behaviour of a company's users in relation to the services they access and the places from which they access. In case of abnormal behavior, generate an alert so that this access can be managed and prevent improper access.
-
Intrusion detection system (IDS), we analyze the behavior of human beings in their daily relationship with the company's services, in this way, when someone operates with unusual location behavior, your system will report them as an intruder thanks to our IDS, being able to avoid inappropriate access in time.
-
Get an easy and secure user authentication, provide your employees with the easiest authentication system. While these will operate with peace of mind and without any tedious method, Ironchip's intelligent location will be transparently guaranteeing the security of your accesses.
-
Passwordless, without passwords, without codes. With Ironchip, workers will receive a notification in the mobile/computer application that they will validate and in that moment they will be guaranteeing that they are who they say they are, with three identity tests: user, device intelligence and mobility behavior.
-
Respect the privacy of the employees and comply with the current RDGP, the intelligent location is totally anonymous, in addition we only store the prediction algorithm capable of determining if the location is valid.
-
It is a 100% adaptable solution to your needs: integration in any service in an agile and comfortable way. Protect your access to VPN, Outlook mail, Windows Log on, Azure Cloud...)
- It works with the devices that your users use every day, since we have a multidevice MFA, mobile, desktop, laptop... With any operating system Android, iOS, Windows, macOS, Linux...
-
Even with a fully customized authentication application adapted to your identity to generate a culture of security within the company.
Protect your users through intelligent location, generating a safer and optimal environment for work with various solutions as you can imagine:
- Secure login on Windows computers.
- Protect your remote access to VPN, RDP...
- Secure connection to Microsoft Exchange (Outlook) mail.
- Login protection in Office 365, Google services Azure Cloud...
- And thousands more solutions, ask us!